Policies and Implementation
Mobiloan has placed a primary emphasis on the development of a secure multi-platform application.
Overview
Security Measures, Processes and Policies
Mobiloan has been designed with security considerations at it’s core.
Microlenders throughout South Africa rely on Mobiloan for the provision of a reliable Loan Origination and Management System.
Mobiloan has comprehensive operational security controls and measures in place, keeping our customers’ data and intellectual property safe.
Mobiloan and it’s platform and integration partners have each passed stringent security reviews, allowing us to deploy safe and robust applications that work with sensitive information.
Protection of PI and PIIP
Mobiloan instances often contain valuable and sensitive information.
We are serious about protecting such sensitive information, whether it is personal information (PI), proprietary information, or intellectual property (PIIP) that is used by, or contained within an app.
We continuously work to ensure that Mobiloan is safe, and that our processes and internal controls are best-in-class.
Application and Data Security
Mobiloan is responsible for securing the application.
Mobiloan also ensures that all integrations with third party service providers are also secure.
This is done by leveraging various technologies. One such technology is SSL (Secure Socket Layer) / TLS (Transport Layer Security).
On the other hand, the customer is in turn responsible for controlling access to the application, by making use of and issuing enrolment keys for devices as well as username and passwords for authenticated operators.
This model is known as SSRM: Shared Security Responsibility Model.
Mobiloan is responsible for protecting the application that runs all the services that a customer makes use of.
A customer’s responsibility is determined by physical access and software controls they make use of within their internal control environment as relates to access to the Mobiloan application.
This model ensures that both Mobiloan and the customer as similarly accountable for those items subject to their control.
Evaluations of App Platform
Mobiloan is built on the JourneyApps platform. Below are the list of third-party security reports available for scrutiny.
Mobiloan is built on the JourneyApps platform.
Below are the list of third-party security reports available for scrutiny.

Cloud Security Alliance (CSA) Security, Trust & Assurance Registry (STAR)
Through the CSA STAR program, JourneyApps provides a completed version of the CSA Consensus Assessments Initiative Questionnaire (CAIQ), a comprehensive security assessment framework commonly used by enterprises.
The JourneyApps CAIQ is publicly available for download on CSA STAR at the following web address:
https://cloudsecurityalliance.org/star/registry/journeyapps/

Service Organization Controls (SOC) 2 Type 2 Report
JourneyApps performs annual AICPA Service Organization Control (SOC) 2 audits of our platform, and our latest SOC 2 Type 2 report is available to prospective customers and existing customers on request, subject to the execution of a Non-Disclosure Agreement (NDA).
The audit affirms that JourneyApps’ information security practices, policies and procedures meet the Trust Services Principles and Criteria for Security set forth in the SOC 2 standards.

Penetration Test and Vulnerability Assessment Report
The NCC Group (leading global experts in cyber security and risk mitigation) conduct regular security assessments on JourneyApps. At a minimum, assessments are done annually, as well as when any significant changes to the platform are made.
The NCC Group report on the penetration test and vulnerability assessment results regarding JourneyApps is available to prospective customers and existing customers on request, subject to the execution of a Non-Disclosure Agreement (NDA).
Security Measures
Platform Architecture
Application Architecture
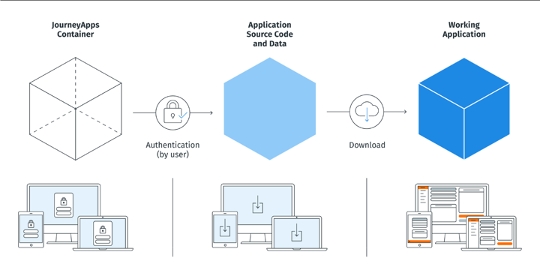
Users install Mobiloan “containers” that contain no customer proprietary information.
Containers can be distributed via Mobile Device Management (MDM) software or other means. Once users securely authenticate in the container, their proprietary custom application and data are downloaded.
Authentication methods supported: JourneyApps Standard and custom REST authentication.
Cloud Environment
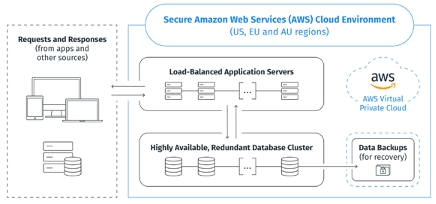
Application servers and database servers for JourneyApps run in a virtual private network on Amazon Web Services (AWS).
JourneyApps runs on a redundant load balanced cluster which is horizontally scalable and resilient against single points of failure. If any single server fails, there are redundant servers which can take over the load seamlessly. The cluster’s redundancy is further supported by hosting in multiple isolated failure zones.
User Management and Permissions
Only authorized users can obtain access to applications or data.
Any user’s access can be revoked, and sensitive application data can be remotely deleted by administrators.
Roles and customized permissions can be assigned to each user.
Data Encryption
Data is encrypted end-to-end on JourneyApps:
At Rest: Data stored in the platform uses block-level encryption (AES-256).
In Transit: Data in transit is encrypted using TLS V1.3.
In Use: Data stored and used in applications are encrypted on the device. On Windows and Android devices, configuration of an application PIN is required for full protection.
Data Synchronization Rules
Mobiloan supports a powerful set of synchronization rules to allow fine-grained control of data that gets synchronized and stored offline on user devices.
Synchronization rules have been customized to meet with the efficiency requirements of the application.
Source Code Encryption
When required, application source code is encrypted using AES-CBC (256-bit key length) and securely stored on each authenticated user device.
Intrusion Detection and Prevention
JourneyApps makes use of an Intrusion Detection System (IDS), and firewalls with restricted ports. Intrusion Detection & Prevention is within the scope of the SOC 2 Type 2 report which is available from the platform provider JourneyApps on request from Mobiloan.
Infrastructure-Level Security
Mobiloan is hosted on Amazon Web Services (AWS), and as a result, JourneyApps leverages the robust controls that AWS has in place to maintain security and data protection in the cloud. AWS provides various certifications and attestations including SOC 1, SOC 2 and SOC 3, and auditing reports are available for review by customers. Please consult the AWS Cloud Compliance and AWS Cloud Security portals for further information.
Mobiloan makes use of several AWS products to provide automatic mitigation of infrastructure and application level attacks. These use a combination of traffic signatures, anomaly algorithms and other analysis techniques to detect malicious traffic in real-time and mitigates attacks with deterministic packet filtering, and priority-based traffic shaping.
Data Access Privilege Elevation and Audit Trails
Comprehensive audit trails are automatically captured by Mobiloan. The audit trails contain information about data access, modification, and where data access privileges have been elevated by Mobiloan staff to access data for issue debugging and system maintenance purposes.
Data Logical Separation
JourneyApps is a multi-tenant environment with logical separation between all application deployments.
An example of an application deployment is “Staging” and “Production” for a specific application.
NCC Group specifically tests the logical separation to ensure that all data is securely sandboxed on the Platform.
Configuration Management
Configuration management is performed using infrastructure automation tools, and changes to systems follow the Secure Development Process described below.
Defense in Depth
Mobiloan follows the Defense in Depth strategy, applying redundancy and multiple layers of technical, administrative and physical controls to prevent security incidents.
Security Patch Management
Mobiloan makes use of automated application and OS-level vulnerability scanning, and further subscribes to security advisories for any vulnerabilities.
Security patches are applied as soon as they become available.
Secure Development Process
The Mobiloan Secure Development Process takes a holistic and integrated approach to security and addresses security concerns during training, planning, architecture design, implementation, and verification. The process includes several practices such as source control, code review and quality assurance to ensure that a good security posture is maintained at all times.
Incident Management Process and Privacy Data Breach Notification Process
The Mobiloan Incident Response Plan consists of six key phases:
preparation
identification
containment
eradication
recovery
root cause analysis
Breach Notification Time Frame: within 24 hours after an incident has been identified.
Data Policies and Disaster Recovery / Business Continuity
The data on Mobiloan always remains the sole property of the customer.
Mobiloan staff only access data when absolutely required in order to support a customer app (in accordance with Data Access Privilege Elevation & Audit Trails described above).
Data Backups are held for 2 months.
Data modification audit logs are kept for 3 years.
Mobiloan aims to exceed our cloud uptime Service Level Agreement (SLA) by providing a highly available platform service running on distributed infrastructure, ensuring redundancy and resiliency. By delivering cloud services with an always-on / always-replicating architecture, the terms Recovery Time Objective (RTO) / Recovery Point Objective (RPO) become obsolete.
On contract termination, all data is handed over to the customer in an open format determined by the customer and then securely deleted from Mobiloan servers.
Staff Policies
Mobiloan:
enforces role-based access for users and administrators.
follows the principle of least privilege — employees should only have the minimum security privileges required to do their job.
observes strict rules in terms of confidentiality — sensitive data is only disclosed to authorized staff.
has formal policies and procedures in place for employment screening, commensurate with the employee’s position and level of access, including conducting criminal background checks.
has a permission control system in place to limit access to system resources.
has an account review and audit process in place to review access to system resources by staff.
ensures that if an employee is terminated, access to all systems is immediately revoked.
Last updated
Was this helpful?